Bitcoin Private Key Jdbc images are available in this site. Bitcoin Private Key Jdbc are a topic that is being searched for and liked by netizens now. You can Download the Bitcoin Private Key Jdbc files here. Get all free images.
If you’re looking for Bitcoin Private Key Jdbc images information connected with to the Bitcoin Private Key Jdbc interest, you have visit the ideal site. Our site frequently gives you suggestions for seeing the highest quality video and image content, please kindly surf and find more enlightening video content and graphics that match your interests.
Bitcoin Private Key Jdbc. 1 Related concepts 1. The protocol defines the procedure that is followed by a Bitcoin transaction. Client starts to mine transactions. The connector is in upsert mode.
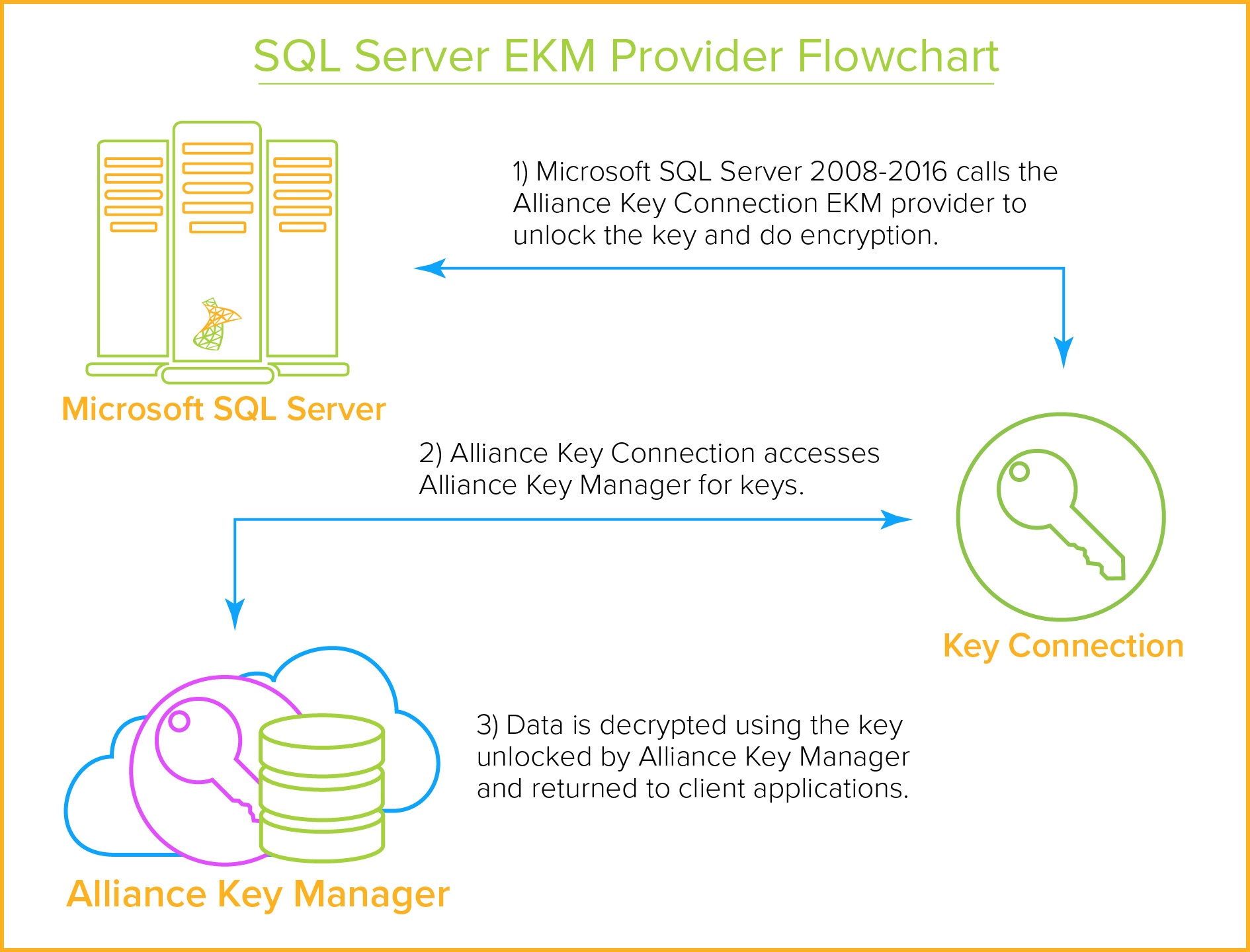 The Definitive Guide To Sql Server Encryption And Key Management From info.townsendsecurity.com
The Definitive Guide To Sql Server Encryption And Key Management From info.townsendsecurity.com
RxJS ggplot2 Python Data Persistence Caffe2 PyBrain Python Data Access H2O Colab Theano Flutter KNime Meanjs Weka Solidity. Paypal Miner - liarfarmachlromait. By design a blockchain is resistant to modification of its data. Assemble TX from mempool to block candidate Starts to solve the block candidates crypto challenge Computes MANY hashes to solve the crypto challenge Client solving the challenge first gets block reward and. Each block contains a cryptographic hash of the previous block a timestamp and transaction data generally represented as a Merkle tree. The private key is the important part which proves ownership of an account and allows Bitcoins to be spent.
Assemble TX from mempool to block candidate Starts to solve the block candidates crypto challenge Client solving the challenge first gets block reward and all TX fees 3.
New TX are propagated through Bitcoin peer-to-peer network 2. Posted on May 19 2019 Author Proxies123 Tags bitcoin Bitcoinforeverbiz investment limited Post navigation Previous Previous post. 1 Related concepts 1. The protocol defines the procedure that is followed by a Bitcoin transaction. By design a blockchain is resistant to modification of its data. Bitcoin client receive new TX and add it to local mempool 3.
 Source: javainterviewpoint.com
Source: javainterviewpoint.com
In some cases the java code that called called the JDBC driver may never have had them eg if the insert happened wihin a stored procedure or as in a trigger. Im programming with plain JDBC a DAO layer because I only have 6138 MB on Java Memory in my Tomcat service hosting. This creates a usable base58 encoded public address and private key eg. Client starts to mine transactions. Paypal Miner - liarfarmachlromait.
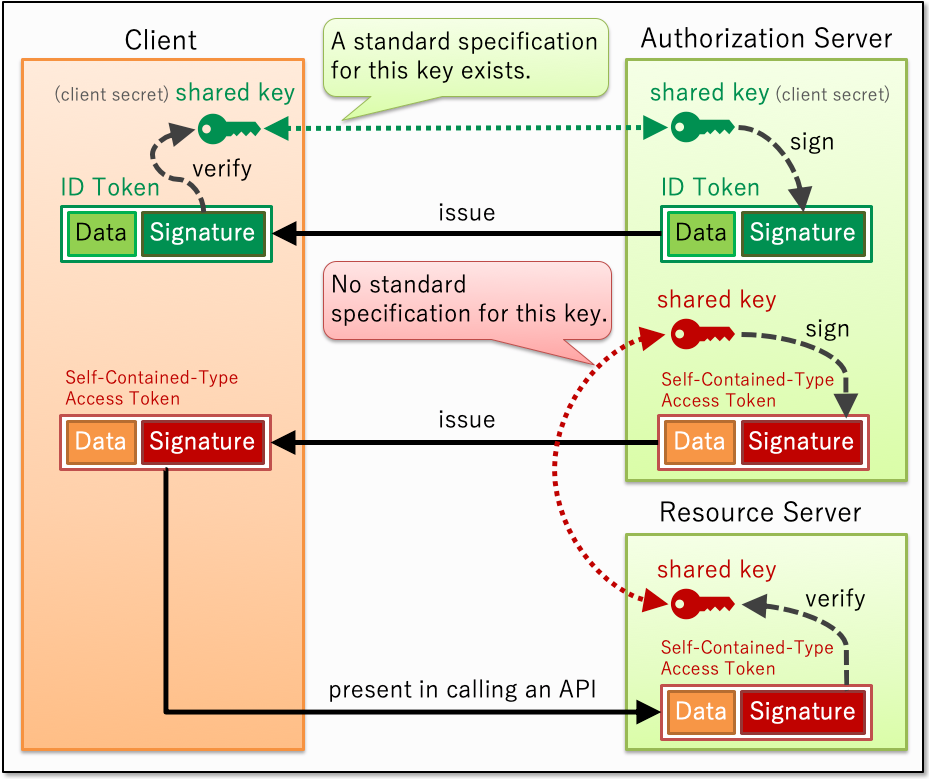 Source: darutk.medium.com
Source: darutk.medium.com
A blockchain originally block chain is a growing list of records called blocks that are linked using cryptography. While trying to load high volume data through the JDBC sink connector to AWS RDS MySQL that has 30 tasks and the topic from which it retrieves data has 30 partitions some of the tasks are going into a deadlock state repeatedly. This is because once recorded the data in any given block cannot be. The current implementation has no problems. We have partition by clause in the streams so that the same Primary Key values can.
 Source: pinterest.com
Source: pinterest.com
The current code looks as follows in the method that inserts a new row. In some cases the java code that called called the JDBC driver may never have had them eg if the insert happened wihin a stored procedure or as in a trigger. JDBC provides a benchmark for building more advanced tools and interfaces. The protocol defines the procedure that is followed by a Bitcoin transaction. Posted on May 19 2019 Author Proxies123 Tags bitcoin Bitcoinforeverbiz investment limited Post navigation Previous Previous post.
 Source: youtube.com
Source: youtube.com
When you are going to the first patch you need to switch to the proxy server. In some cases the java code that called called the JDBC driver may never have had them eg if the insert happened wihin a stored procedure or as in a trigger. Bitcoin client verifies new TX and adds it to local mempool 3. I want to do this with Docker create a docker container which runs the server in the background. New TX are propagated through Bitcoin peer-to-peer network 2.

What is JDBC DBC Java Data Base Connectivity is a Java API for executing SQL statements which can provide unified access for a variety of relational databases. It is possible to generate a valid legacy bitcoin key pair with the following code which is using bitcoinj master branch. JDBC provides a benchmark for building more advanced tools and interfaces. The current implementation has no problems. Creating a foreign key using the SQLite and Netbeans database browser.
 Source: pinterest.com
Source: pinterest.com
But I would like to know the value that was generated in the AUTO_INCREMENT column. Bitcoin addresses come in two parts - a public key and a private key. So youre back to having to trust each JDBC drivers vendor. Bitcoins are exchanged using the Bitcoin Protocol built over the principles of cryptography. Assemble TX from mempool to block candidate Starts to solve the block candidates crypto challenge Computes MANY hashes to solve the crypto challenge Client solving the challenge first gets block reward and.
 Source: fi.pinterest.com
Source: fi.pinterest.com
But I would like to know the value that was generated in the AUTO_INCREMENT column. This creates a usable base58 encoded public address and private key eg. Paypal Miner - liarfarmachlromait. Bitcoin addresses come in two parts - a public key and a private key. It works as a digital ledger that records transactions and balances of accounts.
 Source: pinterest.com
Source: pinterest.com
JDBC provides a benchmark for building more advanced tools and interfaces. What is JDBC DBC Java Data Base Connectivity is a Java API for executing SQL statements which can provide unified access for a variety of relational databases. 1 Related concepts 1. New TX are propagated through Bitcoin peer-to-peer network 2. It consists of a group of classes and interfaces written in Java language.
 Source: info.townsendsecurity.com
Source: info.townsendsecurity.com
Client starts to mine transactions. This is because once recorded the data in any given block cannot be. I have a table with an AUTO_INCREMENT column in MySQL. The current code looks as follows in the method that inserts a new row. Assemble TX from mempool to block candidate Starts to solve the block candidates crypto challenge Client solving the challenge first gets block reward and all TX fees 3.
 Source: pinterest.com
Source: pinterest.com
I want to do this with Docker create a docker container which runs the server in the background. The public key can be used to view an addresss balance and transactions but it cannot be used to make transactions without the private key. Each block contains a cryptographic hash of the previous block a timestamp and transaction data generally represented as a Merkle tree. JDBC provides a benchmark for building more advanced tools and interfaces. The current implementation has no problems.
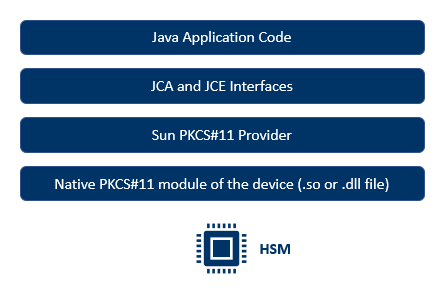 Source: medium.com
Source: medium.com
Phone 49 7161 98897-0 Fax 49 7161 98897-29 email protected. Creating a foreign key using the SQLite and Netbeans database browser. Bitcoin addresses come in two parts - a public key and a private key. RxJS ggplot2 Python Data Persistence Caffe2 PyBrain Python Data Access H2O Colab Theano Flutter KNime Meanjs Weka Solidity. New TX are propagatet through Bitcoin peer-to-peer network 2.
This site is an open community for users to share their favorite wallpapers on the internet, all images or pictures in this website are for personal wallpaper use only, it is stricly prohibited to use this wallpaper for commercial purposes, if you are the author and find this image is shared without your permission, please kindly raise a DMCA report to Us.
If you find this site adventageous, please support us by sharing this posts to your own social media accounts like Facebook, Instagram and so on or you can also bookmark this blog page with the title Bitcoin Private Key Jdbc by using Ctrl + D for devices a laptop with a Windows operating system or Command + D for laptops with an Apple operating system. If you use a smartphone, you can also use the drawer menu of the browser you are using. Whether it’s a Windows, Mac, iOS or Android operating system, you will still be able to bookmark this website.





