Bitcoin Private Key Dkim images are available. Bitcoin Private Key Dkim are a topic that is being searched for and liked by netizens now. You can Find and Download the Bitcoin Private Key Dkim files here. Find and Download all free vectors.
If you’re searching for Bitcoin Private Key Dkim images information related to the Bitcoin Private Key Dkim interest, you have come to the right site. Our website frequently gives you suggestions for viewing the highest quality video and picture content, please kindly search and locate more informative video articles and images that fit your interests.
Bitcoin Private Key Dkim. Private Key Generator V2 4 Full Crack For Mac Endian Firewall Community EFW is a turn-key linux security distribution that makes your system a full featured security appliance with Unified Threat Management UTM functionalitiesThe software has been designed for the best usability. Learn more about How do I add TXTSPFDKIMDMARC records for my domain. I am running Windows 2003 server with Plesk installed. Rob was able to confirm this because the email included DKIM DomainKeys Identified Mail information that GMail was using at the time the email was sent.
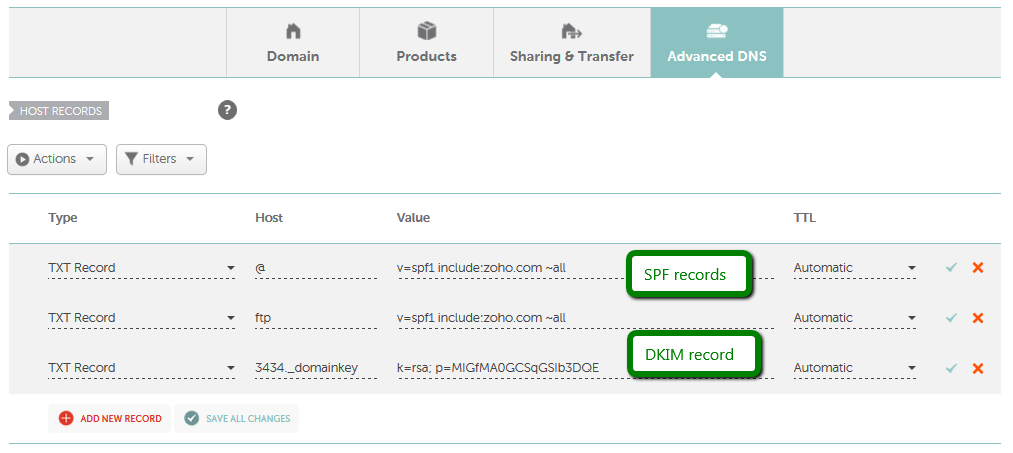 How Do I Add Txt Spf Dkim Dmarc Records For My Domain Domains Namecheap Com From namecheap.com
How Do I Add Txt Spf Dkim Dmarc Records For My Domain Domains Namecheap Com From namecheap.com
They use a mathematical trick of public-key crypto where a pair of matching keys are generated. Learn more about How do I add TXTSPFDKIMDMARC records for my domain. Godaddy 2048 dkim To add a little more detail the 2048 bit RSA key is something called asymmetric cryptography. Something signed with one a private-key can only be verified with the other the public-key. By default Office 365 uses a default signing configuration for domains that do not have a policy in place. This is the public key used during the encrypting process.
Private key that occurs in asymmetric cryptography algorithms such as RSA and Diffie-Hellman as the counterpart to a public key.
Public-key signatures it what underlies Bitcoin. Something signed with one a private-key can only be verified with the other the public-key. If you could find a way to forge these signatures you could instantly make billions of dollars. The solution to the origin authenticity like all fixes to core Internet protocols is kind of a band-aid. I am running Windows 2003 server with Plesk installed. It is a technique which involves having a public key stored as a text record on the domain and having the email server doing the sending sign the email using a private key that is matched to the public key that is stored on the domain record.
 Source: securitytrails.com
Source: securitytrails.com
This is the public key used during the encrypting process. If you could find a way to forge these signatures you could instantly make billions of dollars. It is a technique which involves having a public key stored as a text record on the domain and having the email server doing the sending sign the email using a private key that is matched to the public key that is stored on the domain record. If you do not enable DKIM Office 365 automatically creates a 1024-bit DKIM public key for your custom domain and the associated private key which we store internally in our datacenter. From the crypto point of view for RSA 2048 or 4096 bits is clearly recommended–no discussion on that point.

I generated DKIM for my domain and I received one public key and one private key. When the outbound email server which is serving the mentioned domain sends the email it generates a DKIM signature by its private key and attaches it to the header of the message the email servers owns the private key corresponding to the private one published by TXT record of the domain. DKIM bakes digital signatures into every email sent by a participating mail server. Godaddy 2048 dkim To add a little more detail the 2048 bit RSA key is something called asymmetric cryptography. If you do not enable DKIM Office 365 automatically creates a 1024-bit DKIM public key for your custom domain and the associated private key which we store internally in our datacenter.
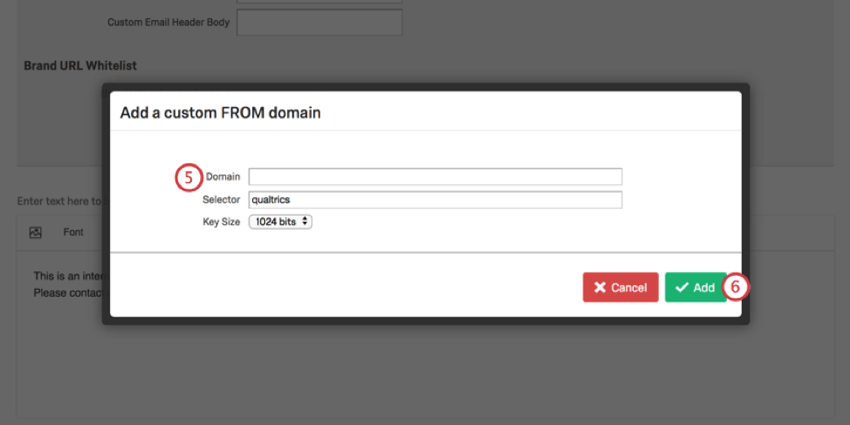 Source: qualtrics.com
Source: qualtrics.com
It is composed of two pieces a public key and a private key. When the outbound email server which is serving the mentioned domain sends the email it generates a DKIM signature by its private key and attaches it to the header of the message the email servers owns the private key corresponding to the private one published by TXT record of the domain. From the crypto point of view for RSA 2048 or 4096 bits is clearly recommended–no discussion on that point. Private key that occurs in asymmetric cryptography algorithms such as RSA and Diffie-Hellman as the counterpart to a public key. It is composed of two pieces a public key and a private key.
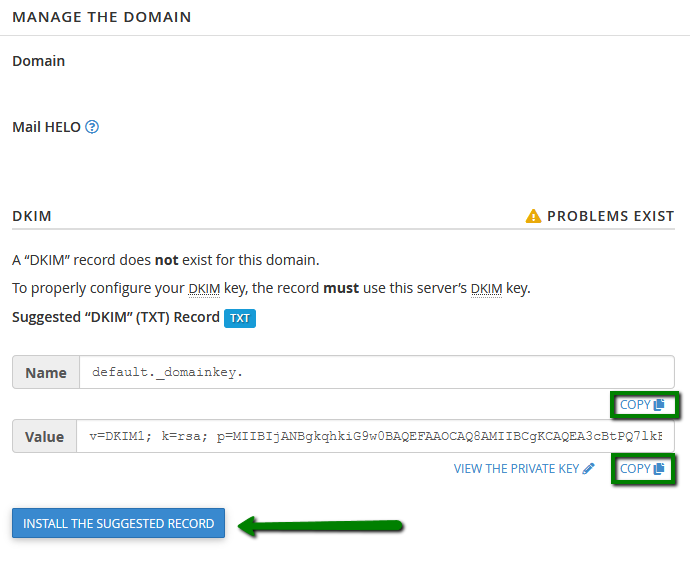 Source: namecheap.com
Source: namecheap.com
Email providers were asked to bolt on an optional new cryptographic extension called Domain Keys Identified Mail or DKIM. How to use this private key. Very easy to install use and manage and still greatly. Something signed with one a private-key can only be verified with the other the public-key. From the crypto point of view for RSA 2048 or 4096 bits is clearly recommended–no discussion on that point.
 Source: youtube.com
Source: youtube.com
Rob was able to confirm this because the email included DKIM DomainKeys Identified Mail information that GMail was using at the time the email was sent. Private Key Generator V2 4 Full Crack For Mac Endian Firewall Community EFW is a turn-key linux security distribution that makes your system a full featured security appliance with Unified Threat Management UTM functionalitiesThe software has been designed for the best usability. The solution to the origin authenticity like all fixes to core Internet protocols is kind of a band-aid. I updated my public key value in my DNS and now I have the private key leftover with me. Learn more about How do I add TXTSPFDKIMDMARC records for my domain.
 Source: br.pinterest.com
Source: br.pinterest.com
Email providers were asked to bolt on an optional new cryptographic extension called Domain Keys Identified Mail or DKIM. I am running Windows 2003 server with Plesk installed. The solution to the origin authenticity like all fixes to core Internet protocols is kind of a band-aid. Private Key Generator V2 4 Full Crack For Mac Endian Firewall Community EFW is a turn-key linux security distribution that makes your system a full featured security appliance with Unified Threat Management UTM functionalitiesThe software has been designed for the best usability. By default Office 365 uses a default signing configuration for domains that do not have a policy in place.
 Source: youtube.com
Source: youtube.com
If you could find a way to forge these signatures you could instantly make billions of dollars. The private key on my ubuntu server is filed under. Find your answers at Namecheap Knowledge Base. Rob was able to confirm this because the email included DKIM DomainKeys Identified Mail information that GMail was using at the time the email was sent. Godaddy 2048 dkim To add a little more detail the 2048 bit RSA key is something called asymmetric cryptography.
 Source: postmarkapp.com
Source: postmarkapp.com
If your target server is the same OS first of all proceed to enable DKIM on the virtualmin DomainKeys Identified Mail you may want to use the same details than the source server in the Domains to sign for section Save this will create the key pairs. If you do not enable DKIM Office 365 automatically creates a 1024-bit DKIM public key for your custom domain and the associated private key which we store internally in our datacenter. I generated DKIM for my domain and I received one public key and one private key. This is the public key used during the encrypting process. The private key on my ubuntu server is filed under.
 Source: namecheap.com
Source: namecheap.com
If your question is not pertaining specifically to the private key usageencodingetc you should use more appropriate tags such as public-key-encryption digital-signature diffie-hellman or even cryptography. If your question is not pertaining specifically to the private key usageencodingetc you should use more appropriate tags such as public-key-encryption digital-signature diffie-hellman or even cryptography. Public-key signatures it what underlies Bitcoin. Last Thursday Rob Graham was able to confirm that one of Hunter Biden emails discovered by the New York Post on the laptop they obtained is authentic. If you could find a way to forge these signatures you could instantly make billions of dollars.
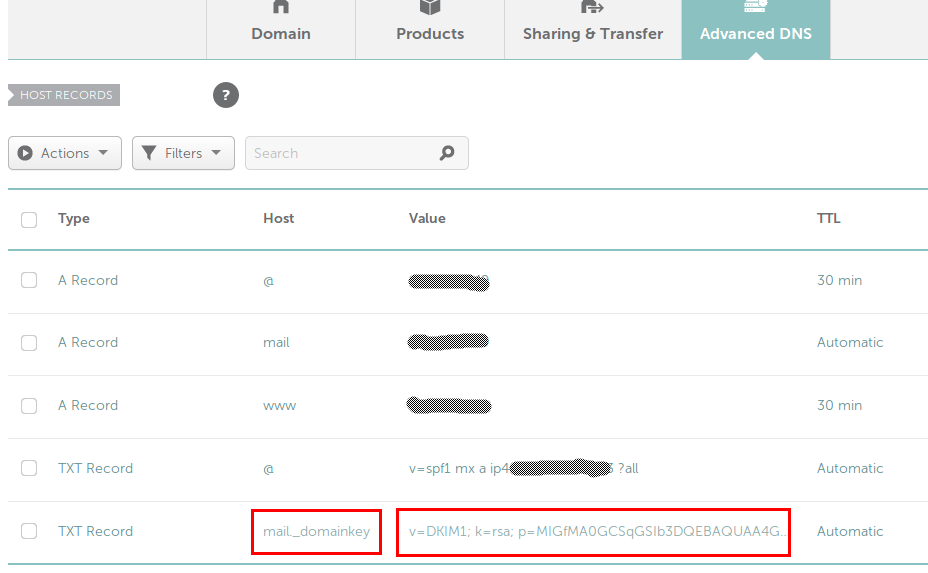 Source: linuxbsdos.com
Source: linuxbsdos.com
By default Office 365 uses a default signing configuration for domains that do not have a policy in place. I generated DKIM for my domain and I received one public key and one private key. Im currently thinking about a 1024-bit key vs. From the crypto point of view for RSA 2048 or 4096 bits is clearly recommended–no discussion on that point. DKIM bakes digital signatures into every email sent by a participating mail server.

DKIM DKIM stands for Domain Keys Identified Mail. Last Thursday Rob Graham was able to confirm that one of Hunter Biden emails discovered by the New York Post on the laptop they obtained is authentic. What is the recommended key length for DKIM. From the crypto point of view for RSA 2048 or 4096 bits is clearly recommended–no discussion on that point. Email providers were asked to bolt on an optional new cryptographic extension called Domain Keys Identified Mail or DKIM.
This site is an open community for users to do submittion their favorite wallpapers on the internet, all images or pictures in this website are for personal wallpaper use only, it is stricly prohibited to use this wallpaper for commercial purposes, if you are the author and find this image is shared without your permission, please kindly raise a DMCA report to Us.
If you find this site convienient, please support us by sharing this posts to your favorite social media accounts like Facebook, Instagram and so on or you can also bookmark this blog page with the title Bitcoin Private Key Dkim by using Ctrl + D for devices a laptop with a Windows operating system or Command + D for laptops with an Apple operating system. If you use a smartphone, you can also use the drawer menu of the browser you are using. Whether it’s a Windows, Mac, iOS or Android operating system, you will still be able to bookmark this website.





